The Importance of Caution When Choosing Browser Extensions
Browser extensions have the potential to access a significant amount of your online activity, making it crucial to carefully evaluate which add-ons you choose to install and permit in your browser.
While many extensions are trustworthy and genuinely beneficial, there are also some that pose risks. Security researcher John Tuckner, as reported by Ars Technica, uncovered numerous questionable extensions requesting excessive permissions and appearing to mine user data. Alarmingly, these suspicious extensions are reportedly used by about six million people.
Many of these extensions are not listed in the Chrome Web Store, meaning users must visit specific URLs to access them, which decreases their visibility to security checks. Additionally, they often lack substantial features and are designed in ways that obscure their true functions.
Worryingly, some developers of these extensions have received a “Featured” designation from Google, which suggests they have met certain standards for privacy and security. This serves as a reminder that just because an extension appears legitimate, it’s essential to remain vigilant.
While there is no guaranteed method for identifying suspicious browser extensions, there are several strategies to evaluate their legitimacy, which will be detailed below.
Stay Informed
Following trustworthy sources in the tech community can keep you informed about security and privacy developments, much like John Tuckner does. Keeping up with current tech news and trending stories on social media can provide insights into any emerging issues.
For instance, consider the Honey extension that was recently found to employ dubious methods to manipulate online prices. Being well-informed allows you to learn about such findings promptly.
Examine User Feedback
While reviews can sometimes be misleading or fabricated, they can offer valuable insights. Pay attention to recurring issues and concerns highlighted by users, especially recent posts.
A high number of low ratings can signal potential problems, particularly if users complain about the extension being glitchy or slow. Check whether the developer has responded to these critiques and whether their explanations seem credible.
Credit: DailyHackly
Research the Developer
It’s important to look into the background of the developers responsible for the extensions. Their information is usually available on the extension’s listing page. Investigate what these individuals or teams do and why they would create an extension for your browser.
An extension from a credible developer with a robust online presence and an active GitHub repository generally indicates reliability. In contrast, a developer’s link leading to a poorly developed website with scant information is a red flag.
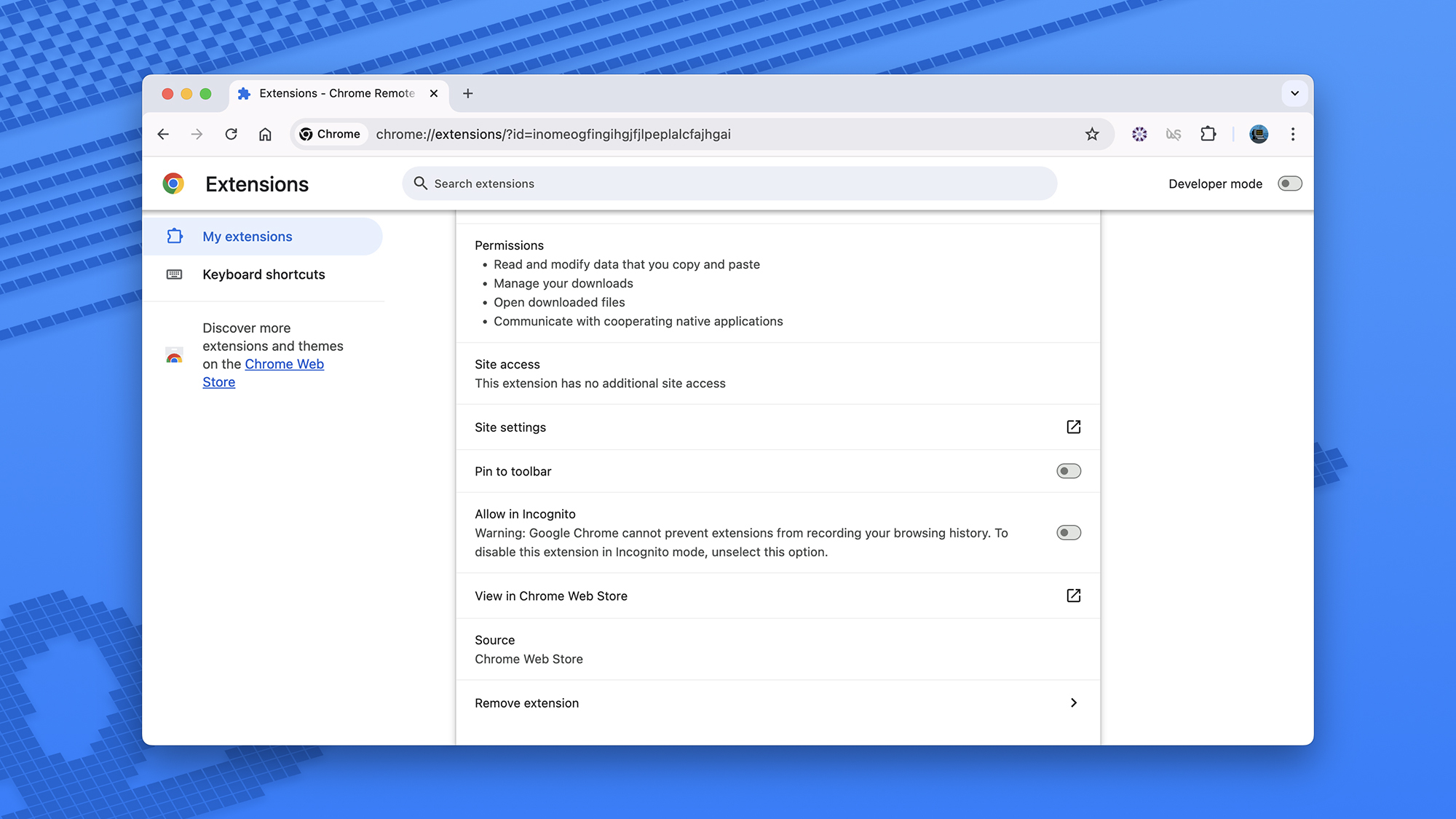
Assess Permissions
Similar to applications on mobile devices or computers, browser extensions request permissions. You can view these permissions on their listing pages, as well as after installation, to evaluate their intended actions.
It’s important to assess what permissions seem reasonable. For example, an extension that manages device tabs has no need to record keystrokes made within the browser.
Credit: DailyHackly
Utilize Security Tools
Several tools can help you identify malicious extensions; one example is Secure Annex by John Tuckner, which utilizes AI to scan extensions for potential issues, mainly geared toward businesses.
For Chrome users, consider tools like Chrome Extension Source Viewer for inspecting code, Under New Management for checking developer backgrounds, and Chrome’s built-in Safety Check. Numerous other options are available across different browsers.
Maintain Updates
Web browsers and operating systems have effectively improved their ability to identify security vulnerabilities, including deceptive extensions aiming to capture data or redirect users to suspicious sites.
Your vigilance in keeping software updated is key, as outdated systems are particularly vulnerable to cyber threats. Ensure that all pending updates for your browser and operating system are installed promptly to protect yourself.












